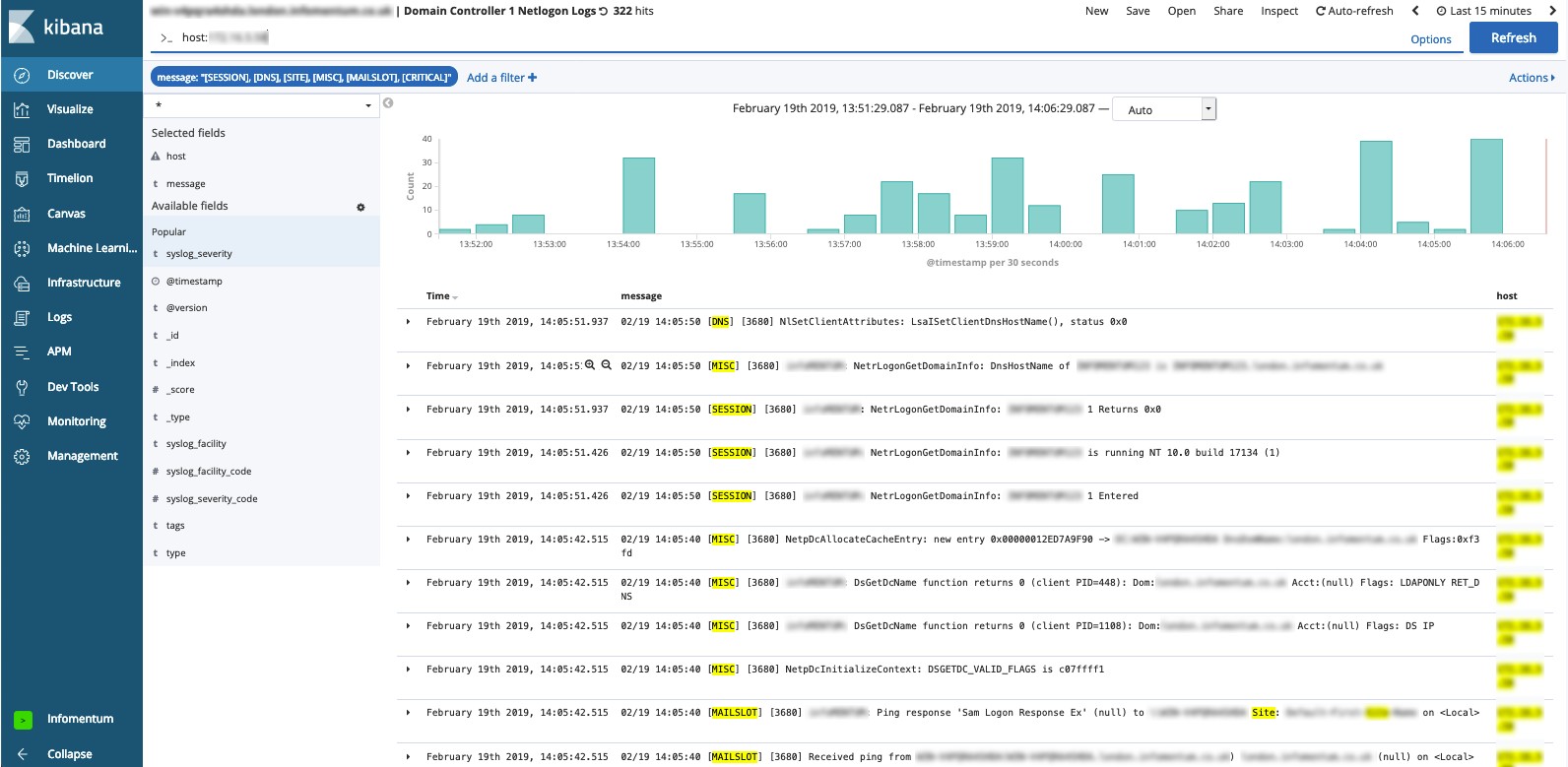
Active Directory Logs To Elasticsearch
I tried setting up a field template called ecs.yml which i got from. Audit logging is disabled by default.
How To Solve The Challenge Of Centralised Logging With Nxlog
We continue with another document where we will try to centralize all our logs in elasticsearch, this time it's up to our fortigate firewalls.
Active directory logs to elasticsearch. The azure module fileset that collects these logs is the activitylogs fileset. For example, users who are assigned the application administrator role within azure active directory may be configured to have the superuser role within elasticsearch. The elasticsearch rest api can be used instead of kibana dev tools as described on this elasticsearch documentation page.
From within the domain controller go. The active directory realm authenticates users using an ldap bind request. Create a new inbound firewall rule.
This is typically the same server (s) you use for authentication, but you can also use a different server if necessary. Whether you want to apply a bit more transformation muscle to windows event logs with logstash, fiddle with some analytics in elasticsearch, or review data in kibana on a dashboard or in the siem app, winlogbeat makes it easy. By default, all of the ldap operations are run by the user that elasticsearch is authenticating.
Azure active directory can also provide a users group membership information within token claims, which can be used to determine which roles a user should be assigned in elasticsearch. Logs are available as.log (plain text) and.json files. This firewall rule will allow the elasticsearch server to query the active directory.
[archy@mikrotik] > ip firewall filter edit 8 log yes [archy@mikrotik] > ip firewall filter edit 65 log yes. Then create a new account, admin. For this blog post, you will log in with local elastic user and use kibana dev tools to create role mappings in elasticsearch, based on the membership of our saml users in active directory groups.
(mainly the ip fields, and dns events) logging an active directory server. The only requirement is that the user to fetch the roles for actually exists on the ldap server. Using ad, you can map groups defined in your windows domain to roles in elasticsearch.
Authorisation is the process of retrieving backend roles for an authenticated user from an ldap server. Winlogbeat’s primary function is to gather windows event logs and ship them to elastic. Kibana ec2 standalone server in.
The default elasticsearch log level is info. To log the events in elasticsearch and use the audit log default settings, simply add the following line in elasticsearch.yml: Managed service for microsoft active directory hardened service running microsoft® active directory (ad).
Nxlog and logstash can be configured to exchange log data between each other in. Assuming you have auditing turned on, you can use winlogbeat to ship event logs to elasticsearch directly. Three master nodes in private subnets;
After authenticating the user, the realm then searches to find the user’s entry in active directory. On the other hand, the bind account will be to query the active directory database. We are only going to install it on the active directory server as we are going to save the elastic agent for our workstation.
Winlogbeat supports elastic common schema (ecs) and is part of the elastic stack, meaning it works seamlessly with logstash, elasticsearch, and kibana. A bind user can be configured and is used to perform all operations other than the ldap bind request, which is. Our ad_kibana_users_group ad group will map to the kibana_user role in.
Your router will now send its syslog to logstash which will then be processed and stored into elasticsearch. I said, the objective is the following, first collect the logs that. To enable it, you need to configure at least searchguard.audit.type in elasticsearch.yml.
The admin account will be used to login to the elasticsearch server as superuser. Logstash is a data collection and processing tool. The shield plugin allows locking down elasticsearch using authentication from the internal esusers realm, active directory (ad) or ldap.
On the domain controller, open the application named windows firewall with advanced security. I am having an issue getting all the winbeat fields mapped to ecs for the elasticsearch siem app. Filebeat is configured to collect and then send the published logs to elasticsearch, but you can easily configure it to do much more, such as monitoring application, container, and system metrics by utilizing prepackaged modules, many.
First, we need to create a firewall rule on the windows domain controller. The active directory realm authenticates users using an ldap bind request. It is often used as part of the elk stack (elasticsearch, logstash, kibana) to collect logs from various sources, normalize them, and forward them to elasticsearch.
This post will explore how to use shield, a plugin for elasticsearch, to authenticate users with active directory. The ids will most likely be different so adjust these before running: On the rpm and debian installations, elasticsearch writes logs to /var/log/elasticsearch/.
This defines the endpoint where the audit events are stored. In some cases, regular users may not be able to access all of the necessary items within active directory and a bind user is needed. On the domain controller, open active directory users and computers.
Create a new account inside the users container. Elasticsearch will by default allow anyone access to all data.
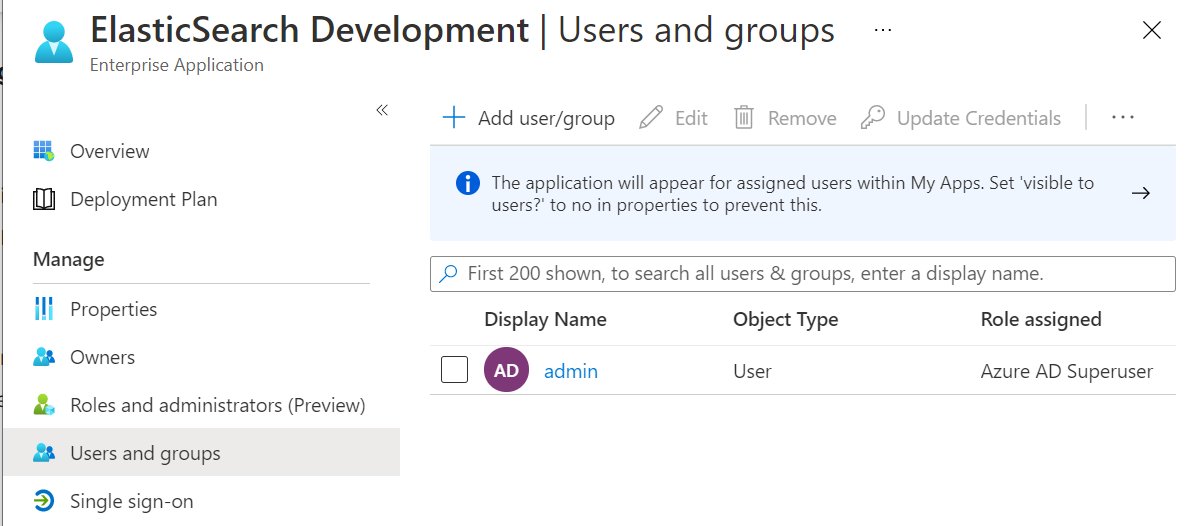
Elasticsearch Elastic Cloud Sso With Azure Ad By Rajat Panwar Medium
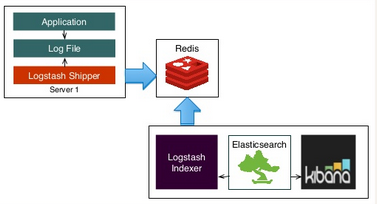
Elk Elasticsearch With Redis Broker And Logstash Shipper And Indexer - 2020
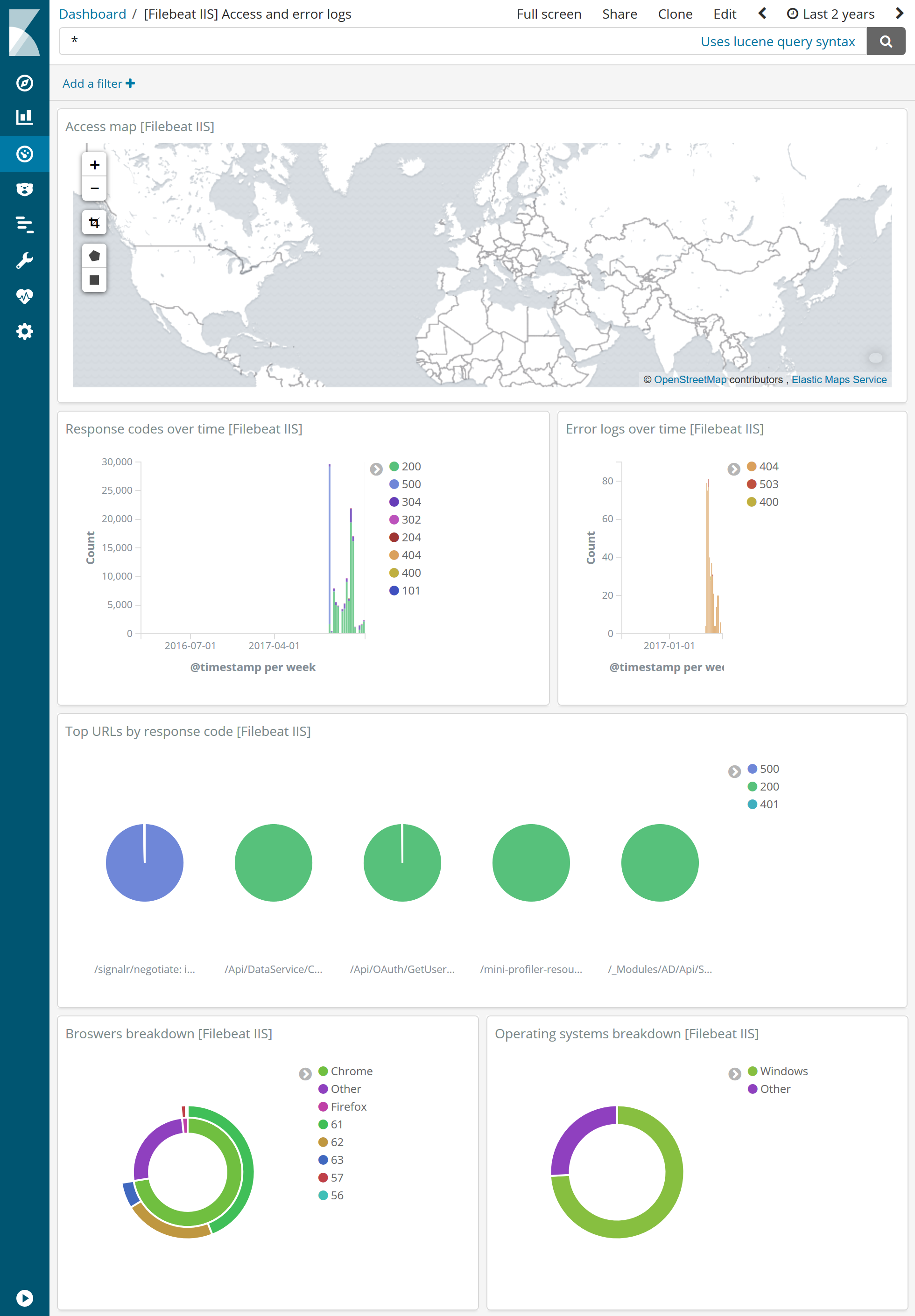
Iis Module Filebeat Reference 68 Elastic

Aws Archives - Page 2 Of 10 - Powerupcloud
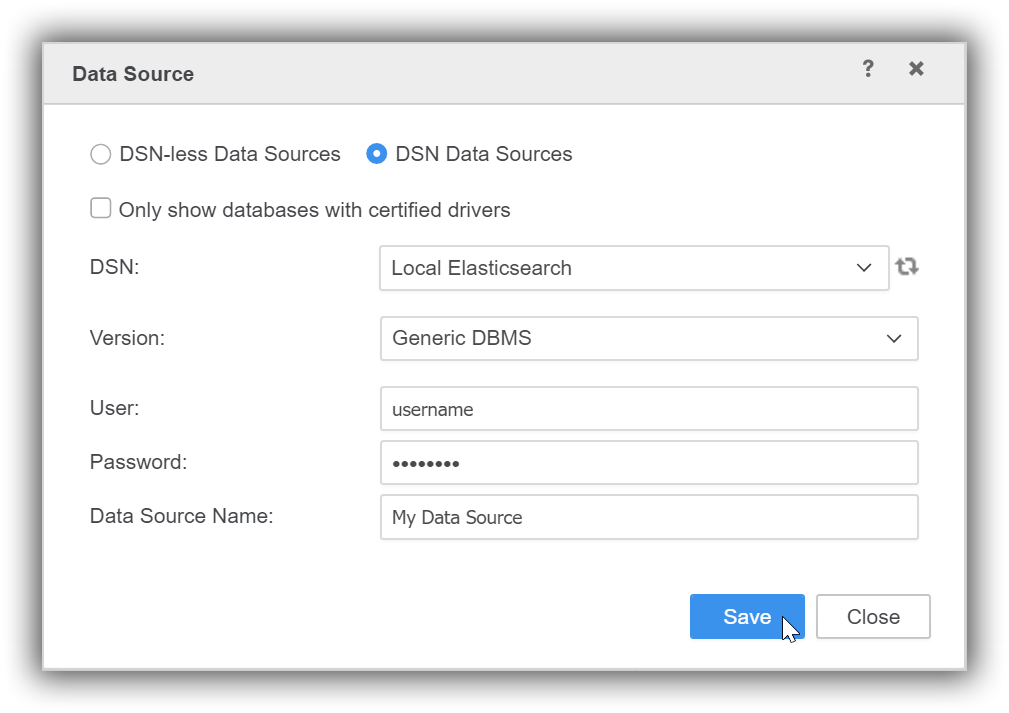
Microstrategy Desktop Elasticsearch Guide 716 Elastic
Data Streams Elasticsearch Guide Master Elastic
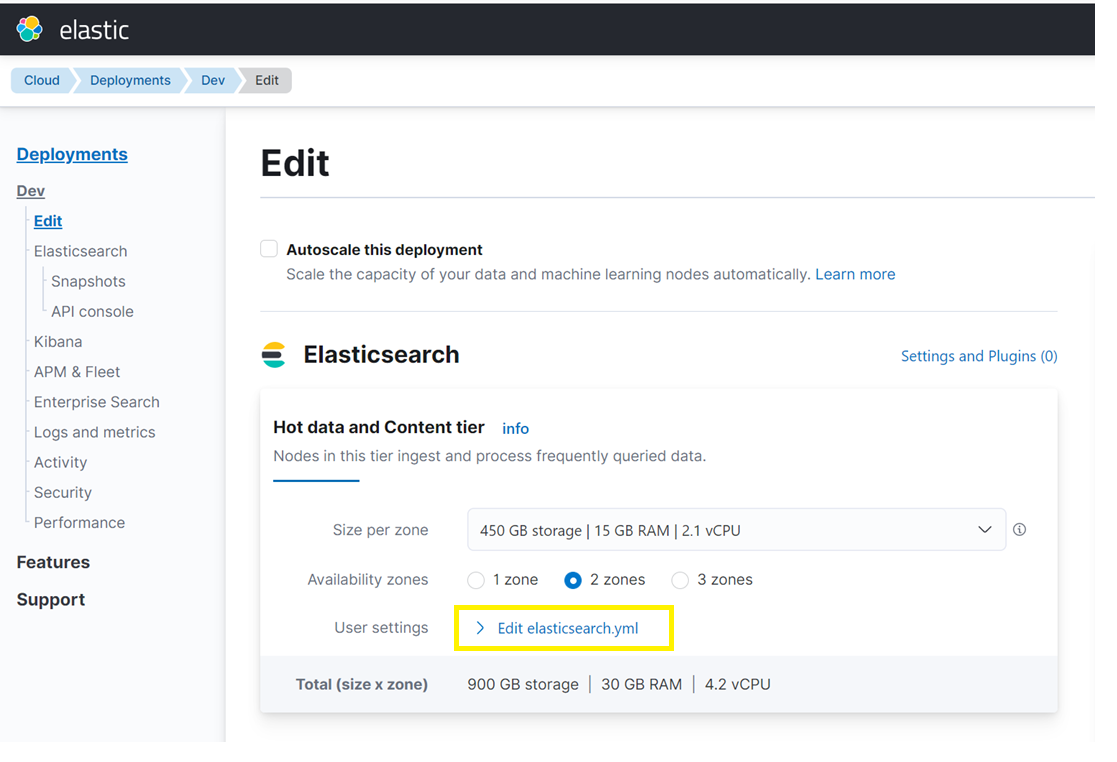
Elasticsearch Elastic Cloud Sso With Azure Ad By Rajat Panwar Medium

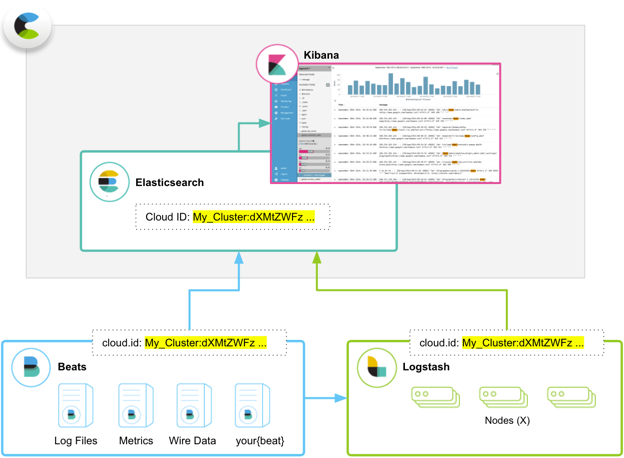
Configure Beats And Logstash With Cloud Id Elastic Cloud Enterprise Reference 26 Elastic
Data Streams Elasticsearch Guide Master Elastic
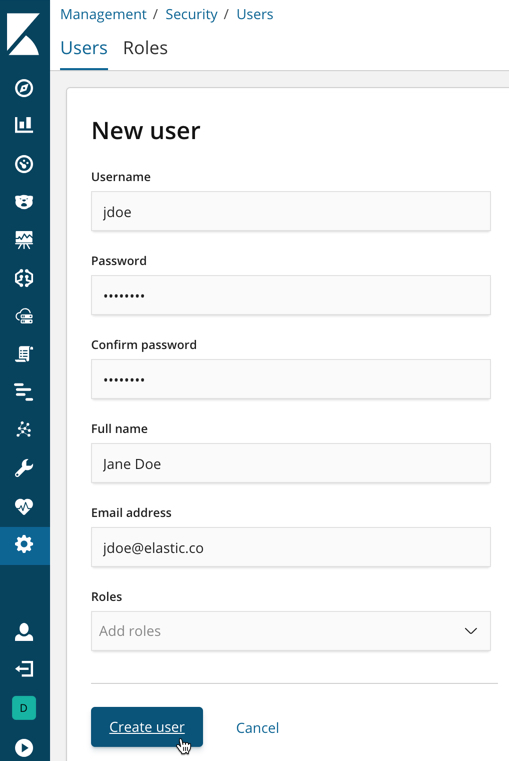
Create Users Elasticsearch Guide 68 Elastic
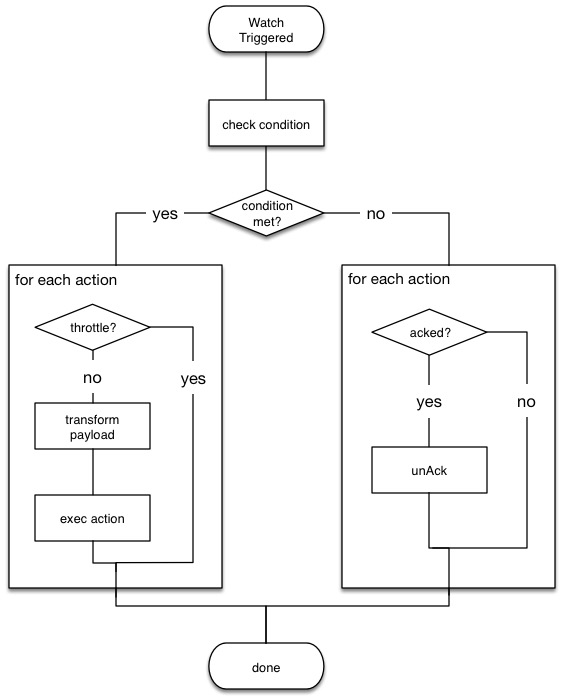
How Watcher Works Elasticsearch Guide 716 Elastic

How To Enable Secure Access To Kibana Using Aws Single Sign-on Noise

Exploiting Elasticsearch Visualization In Grafana With Worldmap Blog Bujarracom
Starting Elasticsearch Elasticsearch Guide 716 Elastic
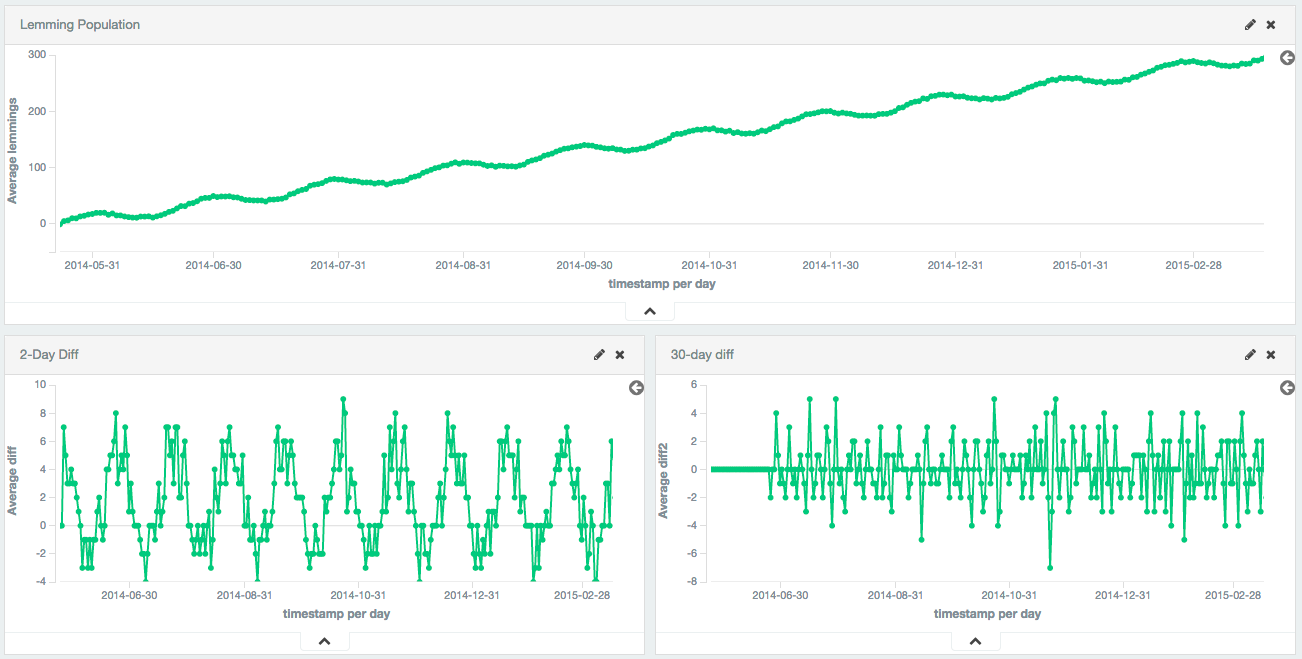
Serial Differencing Aggregation Elasticsearch Guide Master Elastic
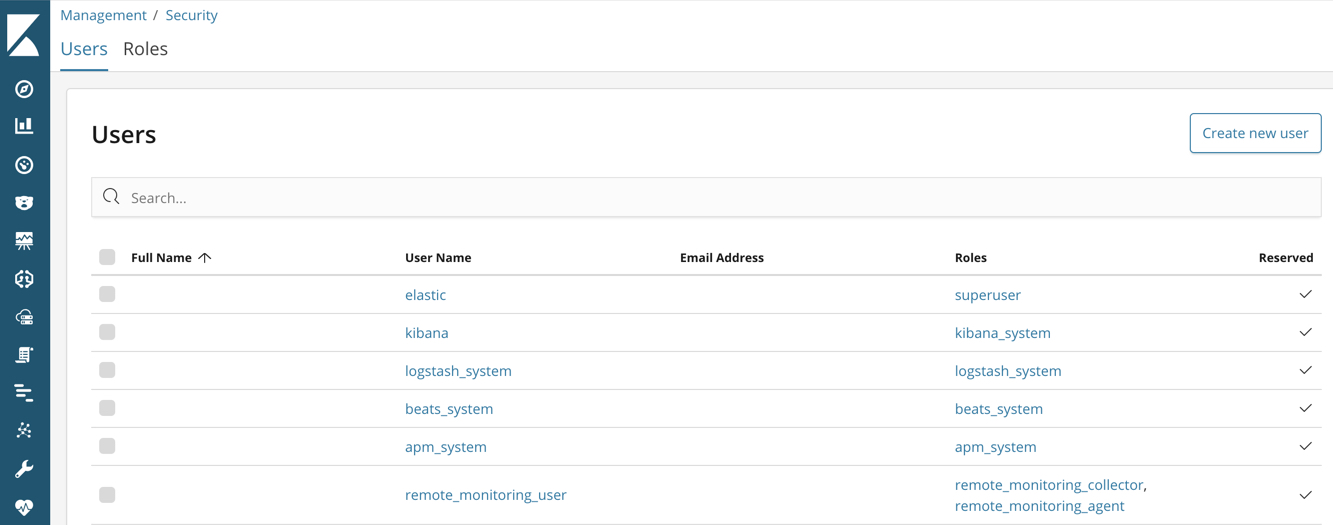
Create Users Elasticsearch Guide 68 Elastic

Elasticsearch Elastic Cloud Sso With Azure Ad By Rajat Panwar Medium

Adaz - Automatically Deploy Customizable Active Directory Labs In Azure Active Directory Deployment Public Cloud
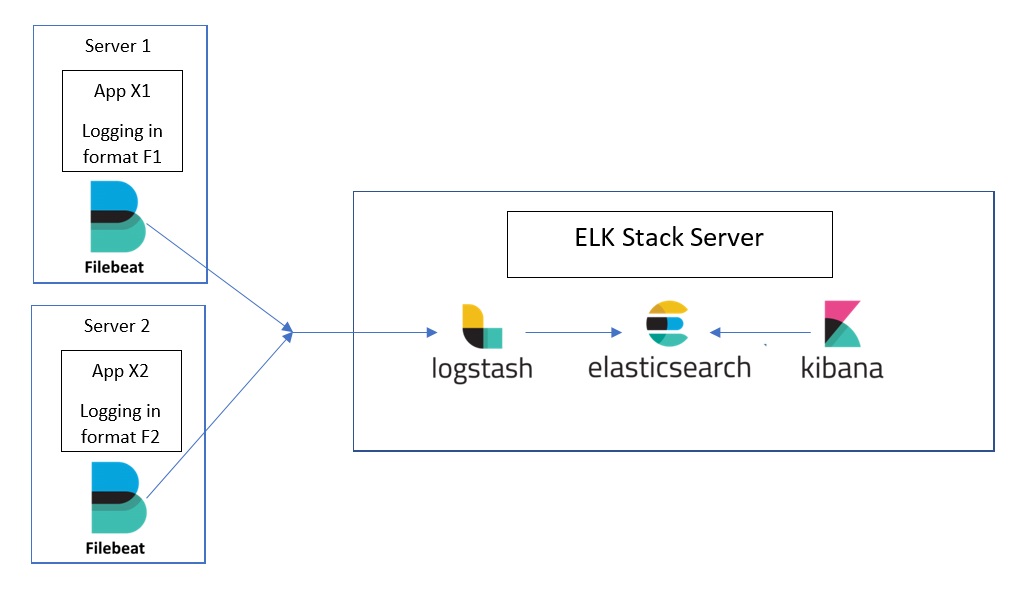
Demystifying Elk Stack Cezary Piatek Blog

